An RODC was created to be used in places where a domain controller is needed but the physical security of the domain controller could not be guaranteed. Few of the important information present in WSDL document are.
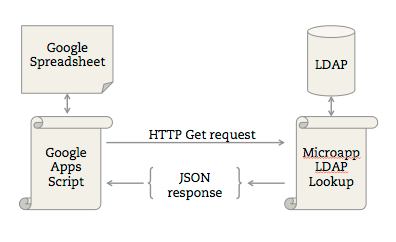
Authentication Protocol Overview Oauth2 Saml Ldap Radius Kerberos
We request candidates to henceforth start focusing on Mains irrespective of your expected scores in prelims 2018.

. Regarding 401 this is from RFC 7235 Hypertext Transfer Protocol HTTP11. If HTTP authentication is not in use and the service has a cookie-based authentication scheme as is the norm nowadays then a 403 or a 404 should be returned. Because it has a slow WAN link.
The Babel protocol. Eg statement route 100008 via 192021 bfd weight 1 via 192022 weight 2 describes a route with two nexthops the first nexthop has two per-nexthop options bfd and weight 1 the second nexthop has just weight 2. Use this password for MD5 authentication of BGP sessions.
Set D Please note. When used on BSD systems see. What topics there are which partitions those topics have which broker is the leader for those partitions and the host and port information for these brokers.
Civil Services Prelims General Studies 2018 This is the final answer key from our side. For example it might be placed in a remote site that is not very secure and has a slower WAN link. Not separated by semicolons.
Installing and Configuring an RODC Explanation. In other words the client needs to somehow find one broker and that broker will tell the client about all the other brokers. Continue reading Insights IAS Final answer.
It is a simple XML document that comes under the Service Description layer of Web Service Protocol Stock and describes the technical details or locates the user interface to web service. WSDL stands for Web service Description Language. Instead all Kafka brokers can answer a metadata request that describes the current state of the cluster.
Cisco Discovery Protocol CDP is a Cisco proprietary protocol designed to facilitate the network management of Cisco devices by discovering hardware and protocol information about neighboring devicesBy using CDP Network Engineers can gather information about neighboring network devices determining the type of hardware or equipment software version. We have explained with justifications all answers to all questions. Wish you all the best.
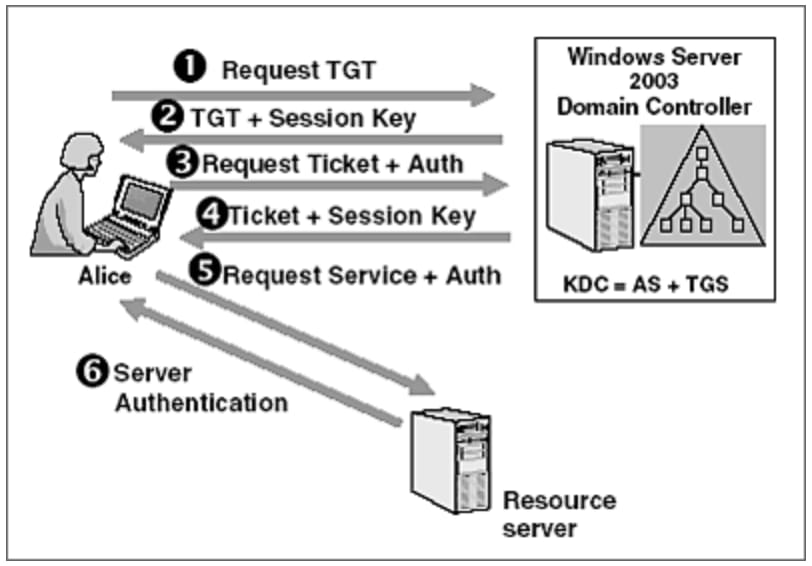
Authentication Protocol Overview Oauth2 Saml Ldap Radius Kerberos
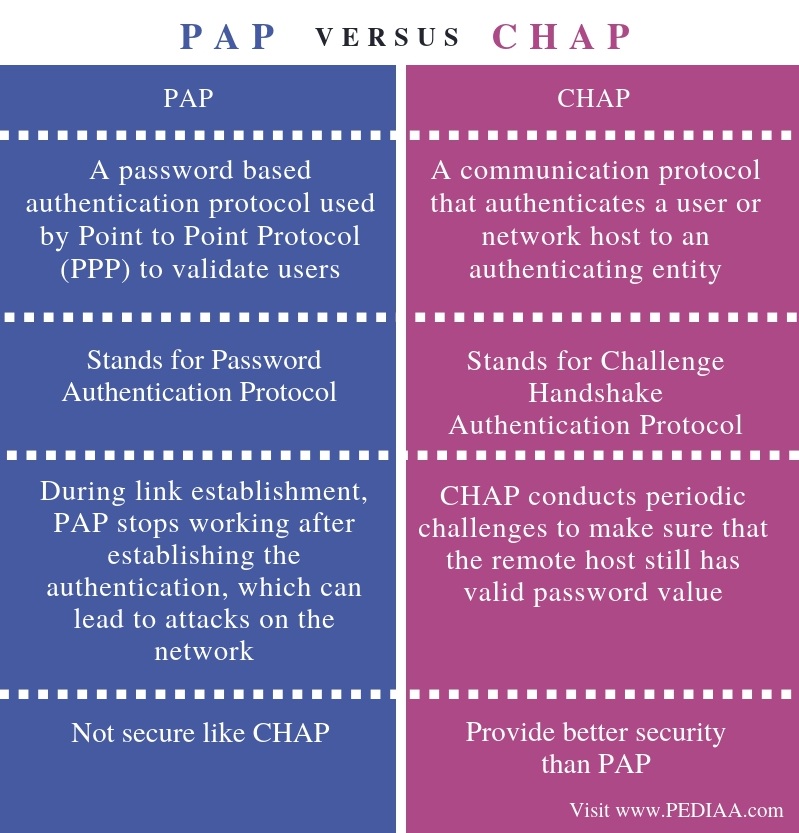
What Is The Difference Between Pap And Chap Pediaa Com

Point To Point Protocols Educational Infographic Computer Network Networking Topics
0 Comments